ANOTHER PERSPECTIVE ON THE PROBLEM OF DIGITAL PIRACY
The Business Software Alliance (BSA) and International Data Corporation (IDC): 2007 Global Software Piracy Study
In its 2007 review of software piracy, a study commissioned by the BSA and performed by the IDC concluded that worldwide losses attributable to software piracy totalled close to $48,000,000,000 (billion). The same 2007 global software piracy study calculated that the weighted average for worldwide software piracy was 38% for newly acquired desktop, laptop, and tablet computers in the countries studied. It should be noted that the BSA has updated these piracy results in subsequent studies.
Credit for 2007 Software Piracy Data:
| Count | Country | Region | Piracy Rate (% Percent) | Piracy Loss ($ Millions) |
|---|
The following table provides a statistical snapshot of the above-mentioned 2007 piracy study.
| Summary | Country | 2007's Piracy Rate | 2007's Piracy Losses |
|---|---|---|---|
| Weighted Average Rate and Total Losses | Planet Earth | 38% | $47,809,000,000 |
| Mean (Average) Piracy Rate | Costa Rica, Mexico, and Oman | 61% | $423,088,496 |
| Median (Middle or Center) Piracy Rate | Turkey | 64% | |
| Maximum (Highest) Piracy Rate | Armenia | 93% | |
| Minimum (Lowest) Piracy Rate | United States | 20% | |
| Mode (Most Frequent) Piracy Rate | Austria, Belgium, Denmark, Finland, Sweden, and Switzerland | 25% |
As the snapshot illustrates, of the countries reviewed in the 2007 software piracy study, the mean or average worldwide piracy rate was 61%, or an average (per country) loss of about $423,000,000 (million). The median, center, or middle worldwide software piracy rate was 64%. The minimum or lowest worldwide software piracy rate was 20%. The maximum or highest worldwide software piracy rate was 93%. The mode or most frequently occurring worldwide software piracy rate was 25%.
Understanding Human Behavior
Naturally, theft or dishonesty is not the only reason why some humans engage in digital piracy. Some additional factors to explain why humans engage in digital piracy include:
- Poverty - Citizens in poorer countries are desperate to join the computer age but cannot afford to purchase the most popular and versatile software applications. Piracy provides one option for the poorer members of society to join and to experience all of the benefits of the computer age.
- Lack of awareness - Citizens are not aware of all available options for consuming software applications such as the existence of open-source, free, and low-cost computing options such as the following ones:
- Convenience and price - For buyers of pirated digital products, the pirated copies are conveniently available at a steep discount below the manufacturer's or retailer's selling price. For sellers of pirated digital products, piracy decreases their business costs and increases their revenue stream.
Perhaps the predominant motivating factor to explain why some humans engage in digital piracy is this: Duplicating and file-sharing technologies make it very easy to anonymously pirate digital content coupled with the small chance of getting caught in the first place and the even smaller chance of being prosecuted in a court of law. Software piracy reduces to another case of the mostly-everybody's-doing-it syndrome. Duplicating and file-sharing technologies cause some humans to compromise or relax their moral and ethical system of values.
The act of copying floppies has become passe and antiquated—albeit the act of copying CDs and DVDs remains popular. Another more persistent, insidious, and pernicious problem for businesses and households alike is the dissemination of computer viruses, malware, phishing, and ransomware as perpetrated by ill-intentioned operators. Accordingly, the next two videos provide brief introductions to malware and ransomware. The next two videos, along with the infographic below, also offer strategies to safeguard against becoming victimized by such crippling computer infections.

To quickly recover from a ransomeware computer infection and to avoid paying the ransom, a comprehensive, ongoing backup strategy is essential. The two strategies mentioned most often is (1) the private, on-premise approach and (2) the public, off-premise approach for safekeeping duplicate copies of the data stored on computers. With the private, on-premise strategy, the household or business firm is responsible for undertaking the backup chores and storing the resultant backups in a safe location (either on or off the premises). With the private, on-premise strategy, the household or business firm also is responsible for purchasing and maintaining the software and hardware required to back up computer data. In turn, the household or business would store the backups in a safe location either on or off the premises. (Note: In this data-storage context, a business firm could be a private business, non-profit organization, religious institution, educational institution, or governmental entity.) As illustrated in the above infographic, ManageEngine is one such business that provides the requisite products needed to implement the private, on-premise strategy. Needless to say, there are numerous other players in the private, on-premise data backup space such as AOMEI, EaseUS®, Paragon Software, Macrium Software, Acronis, and Clonezilla, to name a few such players in this private, on-premise space.
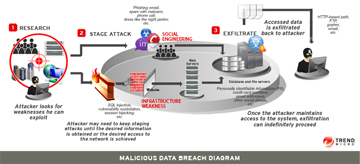
With the public, off-premise strategy, essentially, the household or business firm would contract with an outside vendor for off-premise storage space or to undertake the task of backing up computer data and storing the resultant backup on the vendor's premises. The vendor would safely keep the backups in a secure location controlled by the vendor. With the advent of cloud computing, the public, off-premise strategy has become synonymous with being a public, cloud backup strategy. Again, ManageEngine is one such business that provides the requisite products needed to implement the public, off-premise strategy. Other players in the public, off-premise data backup space include NovaStor, Asigra, MSP360™, Veeam , Backblaze, Amazon Web Services, and Duplicati, to name a few such players in this public, on-premise strategy space. Essentially, the household or business firm would contract with an outside vendor to undertake the task of backing up the household's or business firm's computer data. The vendor would safely keep the backups stored offsite on its servers.
Most computer users are already familiar with popular file-hosting platforms such as Dropbox, Google Drive, Apple iCloud, MediaFire, Microsoft OneDrive, SugarSync, Amazon Photos Storage, Yandex.Disk, and Baidu Network Disk. These file-hosting platforms typically are used to store copies of important documents, photo collections, and so forth. These file-hosting platforms also are used to share files with friends and family members rather than being used to backup all of the data on a computer, including a copy of the operating system and all of the software applications installed on a given computer.
On a related note, another problem to have emerged is the problem of identity theft. This final video offers useful tips to help safeguard against becoming a victim of identity theft.
FLATTER THIS SITE:

SEARCH THIS SITE:
Intellectual Property Disclosures: All videos and songs (as well as many of the images) referenced or spotlighted throughout this website are the legal and intellectual properties of others. All content and opinions on this website (bruessard.com) are those of the author (Edward Bruessard) exclusively and do not necessarily reflect the opinions of the contributors, creators, owners, and distributors of these referenced videos, songs, and images. The author holds no legal interest or financial stake in any of these referenced videos, songs, and images. The contributors, creators, owners, and distributors of these referenced videos, songs, and images played no role at all regarding the appearance of said videos, songs, and images throughout this website; they had no clue that this website would be spotlighting their works.


