HAVING THE CONVERSATION: PRIVACY VERSUS HOMELAND SECURITY
The recent (June 2013) uproar in the USA over privacy versus homeland security has witnessed Big Data's return to the forefront of public discussion. On the "Cloud Computing" page of this website, I mentioned that a central concern of Cloud Computing is data security. When it comes to Big Data, a central concern is privacy.
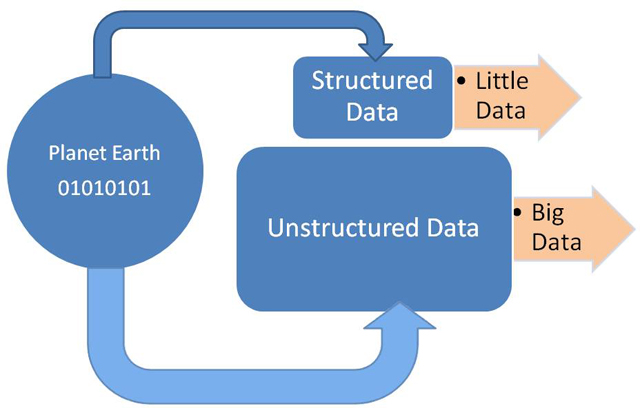
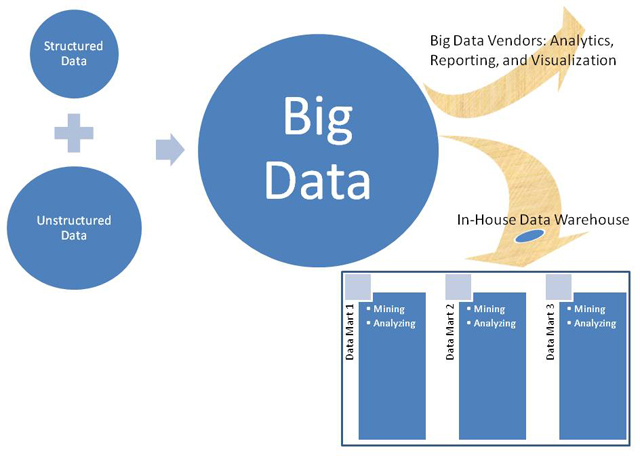
There are two prominent views of Big Data. They are the classic view and the popular view. The top picture above illustrates the traditional or classic view of Big Data. The classic view depicts Big Data as the set of all unstructured data. The bottom picture above illustrates the popular view of Big Data. The second view depicts Big Data as the set of all data, both structured and unstructured. Big Data, in turn, is queried for information by various interested parties (such as governments, corporations, and universities) using various technologies.
Big Data was made possible by the emergence of the computer and the subsequent spread of the computer across the globe. Factors such as the Internet, more powerful computers, a more versatile and robust hardware infrastructure, a broader spectrum of software applications, a plethora of computer programming languages, assorted web devices, assorted web services (such as social media), and so forth, have combined to result in an exponential growth in all kinds of (digital) data. The essence of Business Intelligence (BI) is the ability to take huge volumes of data and condense it into meaningful and useful information. Summary tables, charts, and maps commonly are generated from Big Data. For instance, the United Nations (UN), among other things, made effective use of charts and maps to summarize its global population data:
XML-related technologies also are used to organize, extract, transform, and assemble relevant bits of Big Data into various formats. The ultimate objective of Big Data is for users to gain insight, knowledge and wisdom from the data.
The uproar over personal privacy in the USA raises some important questions that all human societies must address as humans prepare for 22nd century living. These questions include: Must humans engage in certain activities simply because existing technology allows these activities to happen? For instance, should humans destroy Earth simply because nuclear weapons technology permits them to do so? Is surveilling the activities of all citizens the best approach to prevent an act of domestic terrorism? Should certain private corporations reveal your every movement to the world simply because, say, their artificial satellites and Global Positioning System (GPS) technology permit them to do so? Should Internet companies broadcast your 24-by-7 whereabouts to the world simply because face-recognition technology (coupled with smartphones linked to social media) permits them to do so? Simply because some corporations possess much of your personal information or know a great deal about your online or World Wide Web viewing habits, must they turn around and sell bits and pieces of that information to the highest bidding marketing companies?
These kinds of global privacy concerns are completely new to the world. The present generation of humans is the first one in the history of Earth to live in a globally connected world of ubiquitous technology whereby privacy almost has become a thing of the past. Almost all of the electronic gadgets in use today (for example, tablet computers, digital cameras, smartphones, and so forth) generate some sort of traceable digital signature when they are used to create output. Almost all online activities generate some type of traceable digital trail (for example, email messages, instant messages, online postings, chat room activities, and so forth). Sometimes you might think that you are doing something anonymously, but, in reality, you really are not (that is to say, you really are not anonymous in the sense that certain interested parties probably are not determined to retrieve all of your personal data, which generally is the case and you therefore have the illusion of remaining somewhat faceless online). Artificial satellites in orbit around Earth, among other things, are capable of monitoring human activities. Secretly launched drone flying machines, among other things, are capable of monitoring human activities. Internet connections, too, are traceable to the source (that is, if certain interested parties were determined to perform such traces).
Some USA residents adopt the attitude that they are not doing anything wrong; therefore, they have nothing to fear from being monitored or tracked by the government. However, in the USA, the 4th Amendment of the Constitution states, "The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized."
Other USA residents view the USA's government tracking of users's telephone calls and users's Internet activities as an "unreasonable search" given that most users are neither suspected of engaging in any type of terrorist activities nor are they remotely interested in engaging in any type of terrorist activities. (Whether or not the courts would agree with their "unreasonable search" argument is a completely separate matter.) The USA government's monitoring of telephone activities throughout the country to proactively combat terrorism, whether those being monitored are innocent or not, is analogous to all teenagers in a city being placed under curfew to proactively reduce the incidence of juvenile delinquency (including the vastly more numerous, innocent teenagers who have never gotten into trouble with the law). The USA government's monitoring of telephone activities throughout the country to identify terrorist suspects, in part, is accomplished through the use of Big Data and the deployment of Big Data tools.
Before the September 11, 2001 terrorist attacks in the USA, the USA government used to infringe upon the privacy of some citizens in the name of preserving national security. These infringements included things such as domestic spying on suspected individuals and groups in addition to other kinds of covert and clandestine activities. After the September 11, 2001 terrorist attacks, the USA government began to infringe upon the privacy of some citizens in the name of proactively combatting and keeping the homeland secure from acts of terrorism. Monitoring the telephone activities of citizens is viewed by some as one way in which the USA government infringes on their privacy.
HOMELAND SECURITY, TERRORISM, BIG DATA, AND OTHER THREATS TO THE USA WAY OF LIFE
If the truth must be told, then the threat to USA national security is not terrorism per se. The real threat to USA national security is an exchange of nuclear weapons with an adversary. Even Big Data is not the most serious threat to privacy in the USA. Perhaps the most serious and urgent threat to USA freedom and the USA way of life is a nuclear war. Most humans do not appreciate the fact that given the existence of nuclear weapons on Earth, on any given day, humans are only minutes away from destroying the world. All it takes is for one international incident to spiral out of control, thus, triggering another world war, which most likely would lead to the end of the world.
Terrorism is a threat to USA national security only in the sense that the terrorists somehow managed to get their hands on some nuclear weapons. As I mentioned on the "Guns and Bombs" page of this website, other threats to USA society and the USA way of life are not acts of terrorism but these other threats include things such as:
- widespread preoccupation with substance abuse and addiction by citizens
Watch (Watch the Trailer for The OxyContin Express)
Watch (Drug Crazed USA)
- the spread of the street gang mentality (of hatred and violence) across the country.
Watch (Belleville Gangs Threaten Violence at Basketball Game)
Watch (Pittsburgh Gangs: Ex-Members Explain the Life, Offer Outreach)
- gunplay and murder, that is, the right of all citizens to bear firearms with everybody walking around strapped, toting a gun, and ready to shoot and kill his or her fellow citizen with it. [The problem with all USA citizens exercising their right to own (and carry) a gun does not reside with the rational, reasonable, responsible, sensitive, respectful, caring, and mild-mannered citizens who own and carry guns. The problem with everybody bearing firearms resides with those in society who are irrational, unreasonable, irresponsible, insensitive, disrespectful, uncaring, hot-tempered, argumentative, and confrontational yet are mingling with the public and carrying their guns. If gun ownership is to be taken to its logical conclusion of everybody owning one, then which is safer for the general public? Is it safer for everybody to be carrying a gun or for nobody to be carrying a gun? Is it safer for human survival for all nations to possess nuclear bombs or for no nation to possess a nuclear bomb? One easily can see how those citizens who have no interest in owning and carrying a firearm can feel threatened and intimidated even by those who appear to be rational, reasonable, responsible, sensitive, respectful, caring, and mild-mannered citizens carrying firearms not to mention feeling threatened by those who appear to be irrational, irresponsible, and quarrelsome gun owners. So, those who do not wish to carry a firearm might feel compelled to carry one, too, if for no other reason than to give the appearance or the impression of being equally threatening and intimidating. Everybody carrying a firearm truly becomes a problem when you throw a little substance abuse (for example, one drink too many), a little bit of bravado, crowds of innocent bystanders including children and the elderly, and so forth, in the mix of those carrying firearms. Take freeway driving, for instance. Can you imagine the outcome of road rage incidents if all drivers carried firearms? Freeway shootouts most likely would become commonplace occurrences. Some of the comments posted to social media websites are downright nasty, rude, cruel, hateful, and hurtful. Those mean-spirited social media comments seem to suggest that there are lots of uptight people in this world. To encourage these uptight people to arm themselves and move around in civil society with firearms is like lighting matches and playing with dynamite. With everyone in civil society walking around toting guns, I do not foresee an outcome of enhanced physical and psychological security for members of civil society. With everyone in civil society walking around toting guns, I foresee civil order breaking down and degenerating into a City of God (Katia Lund and Fernando Meirelles) type of existence. The reason is because, slowly but surely, members of society will begin resolving their disputes with guns. The shoot-first-and-ask-questions-later mentality would become the norm.]
Watch (City of God: Trailer)
- incessant political bickering and stalemate with little vision for the future.
The above videos in this (HOMELAND SECURITY, TERRORISM, BIG DATA, AND OTHER THREATS TO THE USA WAY OF LIFE) section illustrate that terrorism is one of the least threats to the USA way of life. Except nuclear annihilation, the above videos in this section illustrate that perhaps the most urgent threat to the USA way of life appears to be that of USA citizens turning against one another for various reasons. The above videos in this section illustrate that terrorism and Big Data, though important issues, probably should not be at the top of the list of USA national priorities.
BIGGER AND BIGGER DATA, OR VERY BIG DATA
There is little doubt about it. Big Data most likely is here to stay. Big Data most likely is a permanent feature of human existence. There seems to be no turning back the hands of time. The clock keeps ticking. The wheels of progress keep motioning forward into the future.
Websites and videos such as the following ones are demonstrating how it increasingly is becoming impossible to escape the reach of Big Data in the modern world:
The following two videos illustrate the positive potential for Big Data to improve the human condition. These two videos also illustrate how Big Data is queried and transformed into meaniful information.
BIG DATA AND BIG FUN
Say, for instance, you were in the mood for having some big fun. You wanted to visit one of the world's amusement parks or one of the world's recreational parks. The problem is that you are not aware of the available park options. The Big Data phenomenon is all about aggregating and sifting through mountains of disparate data to extract relevant, useful, and beneficial information. Data mining derives its meaning from sifting through mountains of data in an effort to extract informational gems, nuggets, or diamonds. For instance, by using its Search and record-display features, the table below simulates how it is possible to navigate through mountains of data to easily and quickly locate available parks to visit.
| Country | Park Name | Map | Latitude | Longitude | Feature | Timezone |
|---|---|---|---|---|---|---|
| Country | Park Name | Map | Latitude | Longitude | Feature | Timezone |
Feature Note:
A = Amusement Park
R = Recreational Park
Credit for Data in Table:
GeoNames
The above table contains the names and locations of over 80,000 parks, which were extracted from a broader set of data containing over 8,000,000 (million) records. Most of the 80,000 parks are located in the USA. Undoubtedly, the list of parks in the table is incomplete and remains a work in progress. Nevertheless, the broader point is this: There is always big fun (and big relaxation) in the park waiting to be experienced by all. Big Data aims to show you the way to get there.
BIG DATA CONFESSIONS
In the spirit of Usher Raymond's song titled Confessions, I too, have a confession to make. I confess that even this website utilizes the ClustrMaps, Flag Counter, and Google Analytics web services, which can be viewed as forms of Big Data. These services use the geolocation technique to keep a tally of website visitors including the places of origin of those visits.
In the case of this website, however, I hold absolutely zero interest whatsoever in personally tracing or tracking anyone other than for certifying the number of visits to this website. I respect and honor the privacy of others. The "Visitor Statistics" page of this website serves as a measurement tool and is used strictly to gauge the global popularity of this website. After all, the targeted audience for the book (The Age of Homo Sapiens Sapiens: Heaven or Hell) is all intelligent life forms throughout the Universe including human beings on Earth. In the case of this website, the only thing that I am trying to do is to get you interested in reading the book and to get you to thinking about humankind's future on Earth. Although the book tends to focus on some of the worst aspects of human behavior, and, at times, it examines some controversial topics, the book actually is couched in the language of hope, conciliation, cooperation, courtesy, mutual respect, and positivity for humankind.
Of course, since this website's August 2011 launch, interest in it has been quite low. To be sure, up to this point, this website's popularity has been woefully low when compared to its goal. This website uses the ClustrMaps, Flag Counter, and Google Analytics services because, ideally, it endeavors to attain at least one unique visit from at least 1% of all Internet users in all countries with Internet access. Based on Miniwatts Marketing Group's website, there were 2,433,376,688 (billion) worldwide users of the Internet as of December 2012. The same website indicated that the USA's population was 313,847,465 (million) inhabitants as of 2012. There also were 245,203,319 (million) Internet users in the USA as of 2011. These numbers suggest that, to attain 1% unique visits or a 1% penetration rate in the USA, then this website's tally would need to rise to 2,452,033 (million) unique visits. As of December 2012, this website had attained 2,063 unique visits in the USA, albeit there were many return visits according to ClustrMaps's tally. Obviously, there remains an enormous gap between 2,063 actual unique USA visits and 2,452,033 (million) anticipated unique USA visits. There also remains an enormous gap between 5,937 actual unique world visits (as of December 2012) and 24,333,767 (million) anticipated unique world visits. This website uses services such as ClustrMaps, Flag Counter, and Google Analytics because they provide easy and efficient ways to verify website visits.
PRIVACY VERSUS OPENNESS: THE TRADE-OFF
As humans begin to integrate these ubiquitous technologies into their daily lives, a trade-off has to be made. Humans have to find a way to strike a harmonious balance between privacy (for instance, the presence of no geolocation or no tracking technologies) and openness (for instance, full geolocation or full tracking of their activities and whereabouts). Those who adopt a pessimistic outlook likely would look at the USA's privacy versus homeland security debate as a glass half empty. They most likely would see nothing but gloom and doom emerging from these ubiquitous technologies. The following article by Mathew J. Schwartz exemplifies the pessimistic outlook:
Those who adopt an optimistic outlook likely would look at the USA's privacy versus homeland security debate as a glass half full. They most likely would see nothing but benign possibilities and opportunities arising from these ubiquitous technologies. The following article by JD Lasica exemplifies the optimistic outlook:
Whether as individuals, governments, or corporations, the privacy versus openness debate reduces to a debate over whether humans should deploy these ubiquitous technologies in a benevolent/harmless/non-invasive manner or in a malevolent/harmful/intrusive manner. To further complicate the issue, an activity deemed harmless by some would be deemed harmful by others, which is where consensus and the rule of law come into play. The insightful work of the USA Census Bureau benignly has demonstrated time and again that there is great utility in citizens and businesses being forthcoming and open about certain aspects of their daily activities. The utility resides in the government's ability to make informed decisions. On the other hand, in the private sector, it is becoming abundantly clear that big-data collections on the personal habits of web users are being used for spying, blackmail, and behavioral manipulation purposes, and this trend is an affront to individual freedom.
The final bloc of music videos below depicts the kinds of activities that the USA government most likely will discover upon listening to the telephone calls of citizens. And, for the music buffs, experts, and aficionados out there, as an extra bonus, there also is a deliberate theme or commonality to this bloc of music videos. Did you detect a theme to these music videos? Can you guess what it is? See the "Frequently Asked Questions (FAQ)" page of this website for the answer (that is, FAQ 3).
FLATTER THIS SITE:

SEARCH THIS SITE:
Intellectual Property Disclosures: All videos and songs (as well as many of the images) referenced or spotlighted throughout this website are the legal and intellectual properties of others. All content and opinions on this website (bruessard.com) are those of the author (Edward Bruessard) exclusively and do not necessarily reflect the opinions of the contributors, creators, owners, and distributors of these referenced videos, songs, and images. The author holds no legal interest or financial stake in any of these referenced videos, songs, and images. The contributors, creators, owners, and distributors of these referenced videos, songs, and images played no role at all regarding the appearance of said videos, songs, and images throughout this website; they had no clue that this website would be spotlighting their works.


